Coronavirus has canceled many things, but Black Friday and Cyber Monday may be as big as ever in 2020. Only this year, it will be different.
Some stores promise to end the famous Black Friday sea of bodies clambering over each other for heavily discounted items by offering, for example, no shipping fees for online purchases. And consumer choices on how they shop look set to shift sharply. Google’s US shopper survey found 75 percent plan to buy online more than they did last year. UK retailers point to a surge online shopping since COVID-19 lockdowns hit and urge customers to shop early for Christmas, which will drive more customers to online Black Friday sales.
Black Friday and Cyber Monday are big retail events at the best of times. In the US alone, 2019 online sales on the two days were worth nearly 17 billion US dollars.
It’s not just retailers and consumers gearing up to benefit. Black Friday and Cyber Monday present lucrative opportunities for hackers and social engineering scammers.
To reduce risks and reap gifts this season, retailers need to improve their defenses against cybercrime.
Retail is an attractive target for cybercriminals
Verizon’s 2020 data breach investigations report found financial motivations lay behind 86 percent of attacks. The holiday season excitement is distracting, but businesses can’t afford to let their guard down.
Cyberattacks damage retailers in many ways, like lost sales, loss of reputation and legal sanctions if they’ve not met regulations such as the European Union’s General Data Protection Regulation (GDPR.) The stakes are high on Black Friday and Cyber Monday – in 2019, Kaspersky research identified a range of cleverly designed phishing scams masquerading as seasonal discounts from big brands, almost indistinguishable from the real thing.
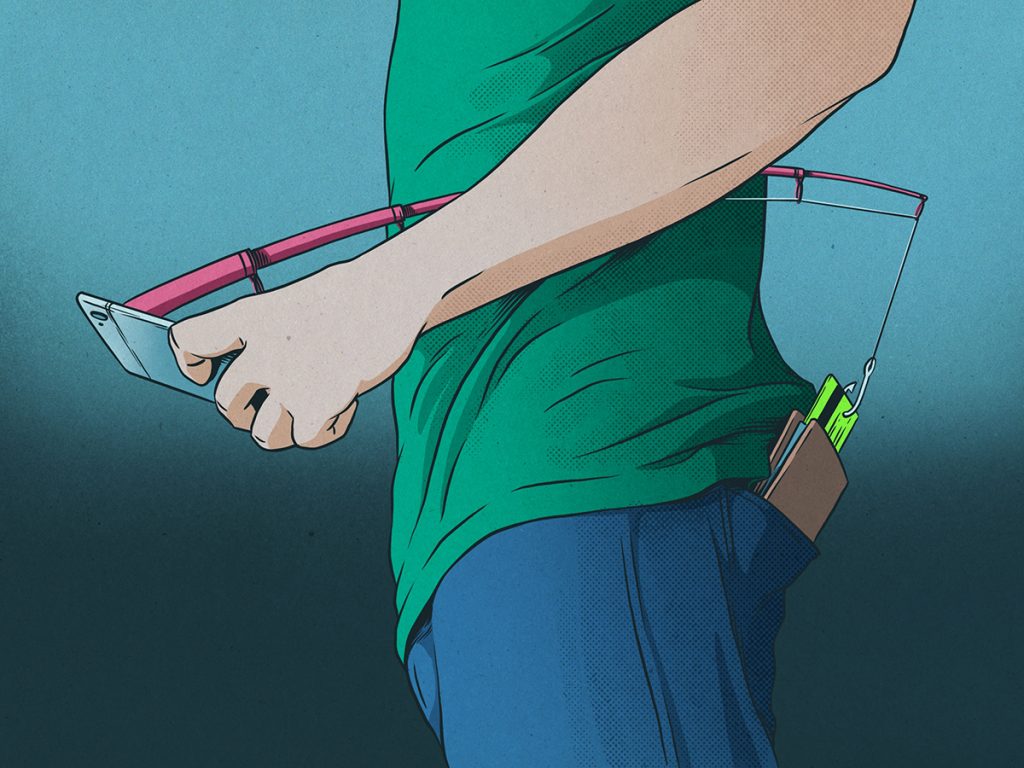
It’s not just phishing emails – smart scammers also launch malicious websites for the occasion to further build a sense that they’re credible.
Scammers know legitimate businesses use the season to create a sense of urgency, with time-limited offers and low prices that are hard to turn down. They use these exact tactics to dupe victims into taking the desired action.
Cybercriminals’ tactics against retail
Cybersecurity advice around the November-December shopping extravaganza is mostly aimed at consumers, but there are two sides to every transaction. Retailers have a duty to protect their customers from scams.
Social engineering attacks depend on scammers being able to convince would-be victims they’re authentic. If an attacker masquerades as your brand, it reflects poorly on you, even if you’re not to blame.
In the holiday season, there’s also a greater likelihood of direct attacks on retailers. You may be too distracted to notice attacks in progress. Hackers can target your website, leading online shoppers to malicious clones to steal their personal or payment information.
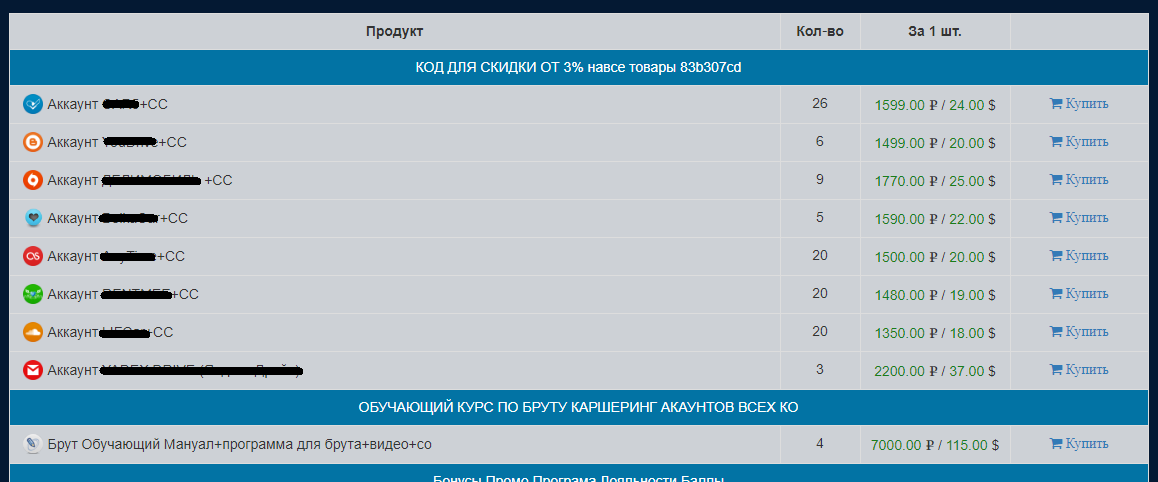
Attackers may plant malicious links and code where consumers click, such as in branded websites and mobile apps. Others might set up fake websites and social media profiles from scratch. Social media and business email are popular ways to attack. By compromising employee accounts, cybercriminals can greatly increase their impact.
Lockdowns and travel restrictions this year will drive more people to buy gifts online and have them delivered directly to the recipient. Mismatched billing and shipping addresses challenge retailers because they may indicate fraud, requiring sophisticated systems or time-consuming manual checks. Often, it will be someone with no recorded purchase history who may have device characteristics not typical of their usual consumer.
How retailers should respond to threats
Be proactive in letting everyone know you’re a step ahead of the threats. See your cyberawareness as a value proposition that drives business growth, rather than just taking care of the necessary. For example, if scammers masquerading as your company target your customers, inform them: Ask them to make sure they check links to your website are legitimate.
Don’t wait for customers to tell you about the scams – look for them. Find and isolate scams posing as your brand and lock down any compromised online accounts before they cause irreparable damage. Look beyond conventional perimeter security (thorough checks for all attempts to connect to corporate resources from outside the infrastructure,) locking down social media and other online endpoints.
National- or multinational-scale retail business should monitor the web around the clock to increase the chances of finding fake websites or other assets disguised as their brand. Threat intelligence or a Security Operations Center are two ways to do it. Monitoring the dark web is also crucial because it’s where criminals sell stolen information and assets.
In the lead up to Black Friday, warn customers you face threats beyond your direct control. Educate them on how to spot social engineering scams, like poor spelling and grammar, and asking for confidential information over email. Remind them of your security and privacy procedures. Tell customers what you’re doing to combat threats and what they can do to be safer when shopping online. Your transparency will build trust in your brand.
Another often-overlooked holiday season threat is distributed denial of service (DDoS) attacks: When hackers bombard servers with requests until they slow to a crawl or crash. For bigger business, ruthless competitors, state-sponsored hackers or political activists may use this tactic, hoping to damage your business finances and reputation. To protect your online store from being taken offline on a landmark retail day, have DDoS protection.
Black Friday and Cyber Monday security challenges are undeniable. Overcoming them will make the holiday season more profitable for your business and safer for your customers. Be honest, transparent and proactive in how you communicate with your customers. Get the right security in place against the kinds of threats your retail business faces, then sit back and enjoy watching the sales roll in.
Author: Claire Hatcher